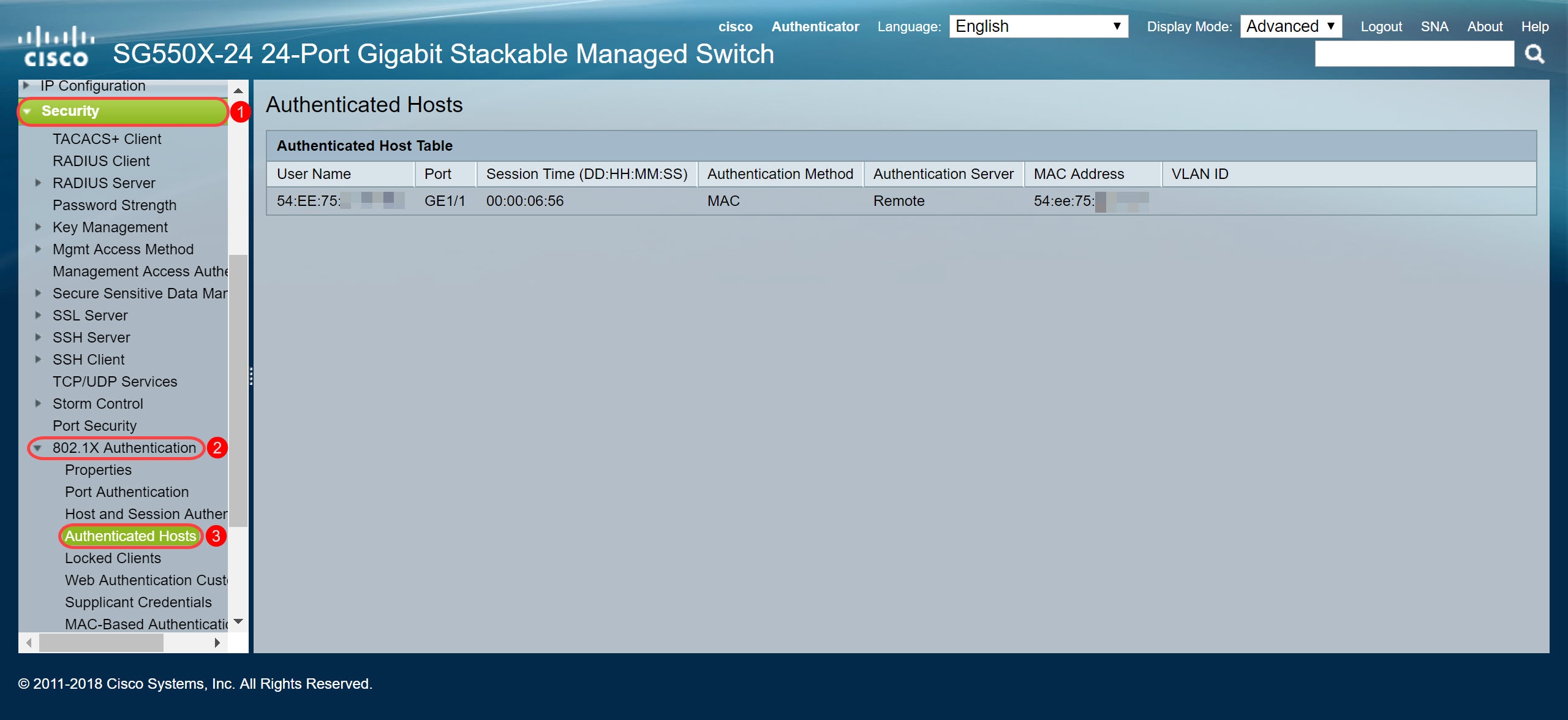
(for local database mac) It seems my authentication only works if i program the mac address of the 'remote' wlc (the wlc holding the AP). This is a pitty, as i was hoping to centralise all 'appoved' mac addresses on the guest controller and not on each individual wlc seperatly. Also, suppose i want a radius server to validate the mac address. This video is an overview of MAC Authentication Bypass. MAB is useful as a method of fallback for bypassing 802.1x authentication when you have an endpoint with no supplicant software installed. Create a SSID with 802.1x (Dont enable MAC filtering) 2. Create identity group 'XYZ' and add the mac address of clients in it. Create a Authentication policy that allows MAB/PEAP and identity store must have AD and Internal host. Create AuthZ policy: Match Identity Group and dot1x and return with desired permission. I hope it will work.
- Mac Authentication Bypass Cisco Wlc
- Mac Authentication Cisco Ise
- Mac Authentication For Cisco Packet Tracer
- Error In Authentication Cisco Enable
1. Components:
Cisco ISE Version 2.1
Cisco switch C3560E with IOS 15.0(2)SE7
Windows 7/8 VMs
2. Network topology:
I’m going to use a very simple topology for this example. NAD (SW1) has connectivity to Authentication Server (ISE) and port G0/9 that goes to a server with VMs. Windows 7 VM’s MAC will be added to ISE’s endpoint database.
3. Configuring Cisco Switch
As a first step we have to enable aaa new model, identify our authentication group and add the ISE server.
Now let’s configure our supplicant-facing port. Something I learned hard way – if port isn’t hardcoded as an access, your switch won’t even take MAB or authentication commands:
So we can either configure switchport as a host, or just hardcode it as an access. I’m going to also assign a VLAN to the port.
Now we can configure mab and port-control as apposed to above
Let’s do the actual configuration
At this point switch configuration is done. We’ll get back to our switch to check some debugs later.
4. Adding NAD to ISE
Go to Administration -> Network Devices
Click “Add” and enter parameters of your NAD. Don’t forget RADIUS shared KEY.
Now let’s add a static entry of our Windows 7 client. From the Home ISE dashboard go to Total Endpoints and then click Add and enter your device’s MAC address.
The configuration is done. Let’s connect our VM and see what happens.
5. Checking debugs on a switch and ISE server
Let’s enable RADIUS debugs on a switch
We can see successful authentication below. Please note the following RADIUS attributes: NAS-Port-Type and Service-Type
On ISE go to Operations -> Live Log and click on authenticated session:
If we scroll down, we can see lots of details for this particular session, but let’s check out why we’ve chosen these particular Authentication and Authorization Policies:
Go to Policy -> Authentication and click on Edit button next to MAB to expand the policy. As we can see, Authentication Policy rule MAB is matched if condition Wired_MAB or Wireless_MAB is met. Meeting one of these conditions triggers authentication from Internal Endpoints.
Now let’s check the actual Wired_MAB condition (as we are connecting to wired switch port). Go to Policy -> Policy Elements -> Conditions -> Compound Conditions and click our Wired_MAB condition in question
Remember our RADIUS attributes from the switch debug? NAS-Port-Type and Service-Type. This is how ISE figures out that we don’t have dot1x supplicant and have to use MAB.
Now let’s check what exactly is happening with Authorization policy. We had Basic_Authenticated_Access being selected in our live logs details. Go to Policy -> Authorization. We can see that condition “Network_Access_Authentication_Passed” is required for Basic_Authenticated_Access policy rule with PermitAccess result.
Network_Access_Authentication_Passed condition name is self-explanatory, but let’s check the condition. Go to Policy-Policy Elements -> Conditions -> Authorization -> Compound Conditions and check our condition in question:
We can see that successful authentication is the only requirement for this Authorization Condition:
So this is what triggers our successful Authorization after Endpoint MAC address is Authenticated against ISE Internal Endpoint database.
We can also quickly check some MAB related stats on the switch. Show MAB all will display ports with enabled bypass.
Interfaces with different authentication methods including MAB can be viewed with show authentication sessions command:
And we can see more session details by looking into interface or session ID. Output should be the same.

This summarizes MAB. It’s not used that much in production environment these days as even very simple devices like printers and scanners can now support supplicants, but I think playing with MAB is a simple way to understand how Authentication and Authorization Policies work in ISE.
In next post I’ll probably have fun with ACLs.
Network Administrators can use port based access control to prevent unauthorized access to the corporate LAN. MAC-Based RADIUS is one method for providing this type of security. This article discusses the benefits of MAC-Based RADIUS and how to configure it in Microsoft NPS and Dashboard.
Benefits of MAC-Based RADIUS
In some environments it is critical to control which devices can access the wired LAN. Ports in common areas make a network vulnerable to access by guests and other unauthorized users. MAC-Based RADIUS can be used to provide port based access control on your MS series switches. Unauthorized users are prevented from accessing to the wired LAN because each device that connects to a switch port will need to be authenticated before network access is granted. Devices are authenticated at the port level with MAC-Based RADIUS. When a device connects to a port with an access policy assigned, before network access is granted, the device must be authenticated by the RADIUS server. The switch (RADIUS client) sends a RADIUS Access-Request to the RADIUS server containing the username and password of the connecting device. The username and password combination is always the MAC address of the connecting device, lower case without delimiting characters. If a RADIUS policy exists on the server that specifies the device should be granted access and the credentials are correct, the RADIUS server will respond with an Access-Accept message. Upon receiving this message, the switch will grant network access to the device on that port. If the RADIUS server replies with an Access-Reject because the device does not match a policy, the switch will not grant network access. It is possible however, to configure the switch to drop devices into a Guest VLAN when they fail to authenticate. The Guest VLAN would provide Internet access only. Below is an example of a basic MAC-Based authentication exchange.
Adding MS Switches as RADIUS clients on the NPS Server
All switches that that need to authenticate connecting devices must be added as RADIUS clients on in NPS. Below are the steps to add the switches as RADIUS clients.
1) Open the NPS Server Console by going to Start > Programs > Administrative Tools > Network Policy Server.
2) In the Left pane, expand the RADIUS Clients and Servers option.
3) Right click the RADIUS Clientsoption and select New.
4) Enter a Friendly Name for the MS Switch.
5) Enter the the IP Addressof your MS Switch.
6) Create and enter a RADIUS Shared Secret (note this secret - we will need to add this to the Dashboard).
7) Press OKwhen finished.
8) Repeat these steps b - g for all switches. See Figure 1 for a sample RADIUS client configuration.

Figure 1.
Create a user account in Active Directory for a connecting device.
1) Open Active Directory Users and Computers: Start > All Programs > Administrative Tools > Active Directory Users and Computers.
2) Create a new user account. the username and password should be the MAC address of the connecting device (letters need to be lower case and it should not have any delimiting characters). See Figure 2 for example user account.
Figure 2.
Configuring a NPS Connection Request Policy.
1) In the NPS Server Console, navigate to NPS (Local) > Policies > Connection Request Policies.
2) Right click on Connection Request Policies, and select New.
3) Name the policy and select Next.
4) On the Specify Conditions page add the following condition: NAS port type as Ethernet (Figure 3) followed by clicking Next.
5) Click Next on the Specify Connection Request Forwarding screen.
6) Click Next on the Specify Authentication Methods screen.
7) Click Next on the Configure Settings screen.
8) Review settings and click Finish on the Completing Connection Request Policy Wizard screen.
Mac Authentication Bypass Cisco Wlc
Figure. 3
Configuring a NPS Network Policy.
1) In the NPS Server Console, navigate to NPS (Local) > Policies > Network Policies.
2) Right click on Network Policies, and select New.
3) Name the policy and select Next. (Figure 4)
Figure 4.
4) On the Specify Conditions page add the following two conditions Windows Groups, this can be the group containing especially for the user accounts created in Part 3. See KB Creating a Windows Group For MAC Based Authentication. For our example we will use DOMAINNAMEDomain Users. Then specify NAS port type Ethernet followed by clicking Next. (Figure 5)
Mac Authentication Cisco Ise
Figure 5.
Mac Authentication For Cisco Packet Tracer
5) Click Next on the Specify Access Permission screen.
6) On the Configure Authentication Methods page, uncheck all options except Unencrypted authentication (PAP, SPAP). (Figure 6)
Figure 6.
7) Click Next on the Configure Constraints screen.
8) Click Next on the Configure Settings screen.
Error In Authentication Cisco Enable
9) Review settings and click Finish on the Completing New Network Policy screen. (Figure 7)
Figure 7.
Creating a MAC-Based RADIUS Access Policy in Dashboard.
1) On the Dashboard navigate to Configure > Access Policies.
2)Click on the link Add Access Policy in the main window then click the link to Add a server.
3)Enter the IP address of the RADIUS server, the port (default is 1812 or 1645), and the secret you created above in part 2. (Figure 8)
4) Click Save changes.
Figure 8.
Apply Access policy to MS Switchports
1) On the Dashboard navigate to Configure > Switchports.
2) Select the port(s) that should have the policy applied.
3) Click the Edit button, make sure the port type is Access, and from the Access policy drop-down select the policy that was created in part 5.
(Figure 9)
Figure 9.
